InterChainZ Project Methodology
This research aimed to answer the core question: “What elements of a trusted third party are displaced by blockchain technology?” by providing a basic demonstrator of distributed ledgers, including blockchains, and comparing how they might work within selected financial services use cases. The research revolves around an online demonstrator of InterChainZ, Z/Yen’s prototype distributed ledger system developed in-house.
Started in June 2015, the research process was divided in six stages, using Z/Yen’s Z/EALOUS methodology.
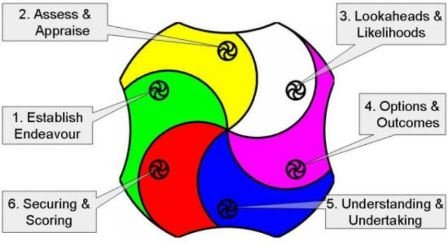
Establish Endeavour
In this first stage of research, the consortium members led by Z/Yen Group agreed the scope, objectives and approach of the research. In particular, it was agreed that the research team would explore several architectures, including Z/Yen’s InterChainZ. The research team started approaching other organisations operating distributed ledger software. The consortium also agreed to contrast and compare selected distributed ledger software on performance, resilience and security by exploring how they worked in the set of four agreed ‘use cases’:
- Identity validation;
- Credit data information sharing;
- Placing a small business insurance policy;
- Placing a motor insurance policy.
Assess and Appraise
The team and consortium members agreed the use cases to be tested and what anonymised data could be supplied for the testing. In parallel, the team sought to approach other organisations known to operate distributed ledger systems in order to invite them to participate by providing their distributed ledger systems for comparative testing. In the event Bitcoin data was easily available for analytical comparison and Ethereum had just launched a new system (Frontier) for which data was readily available. However three other parties who claimed to have 'open source' software proved, despite discussion, not to have software yet ready for comparative testing.
Lookaheads & Likelihoods
The third stage of research centred on uploading data for each use case’s content MDL and consortium members were invited to explore their use case on InterChainZ. R&D focused on validation with three separate validation architectures developed including:
- all nodes - Every node (aka server) can add to the MDL.
- master node - only the Master can add to the MDL.
- supervisor node - the Supervisor needs two other nodes to co-sign in order to add to the MDL.
An independent ICT expert subjected InterChainZ to a security review during the course of the research, concluding, "the system stacks up cryptographically, by which I mean you can use the system to create the kind of non-repudiatable proof you want". However, the more important the system the more attractive it becomes to attack.
Options & Outcomes
In this fourth stage of the research, the team explored storage options and network architectures for InterchainZ. Each use case was expanded to contain not only a Content MDL (with all the documents) but also a related Identification MDL, with the team exploring different levels of interactions between the two chains. The team also sought to test the scalability of InterChainZ by increasing the number of servers across which the prototype runs.
Understanding & Undertaking
The team collated preliminary findings stemming from previous stages, including issues and possible recommendations for future R&D efforts. A user guide was created and circulated to all consortium members. A sense-making session was organised with the research consortium members to discuss the findings and recommendations and how these should be presented.
Securing & Scoring
During this final stage, the team worked to finalise web-based materials including:
- An overview of distributed ledgers;
- A user guide for InterChainZ;
- The overall findings from this phase of work, including related videos and graphs;
proposed recommendations for future research.
Articles & Reports
- The Economic Impact Of Smart Ledgers On World Trade
- Liquidity Or Leakage - Plumbing Problems In Cryptocurrencies
- Get Smart About Scandals - Past Lessons For Future Finance
- The Quantum Countdown: Quantum Computing And The Future Of Smart Ledger Encryption
- Smart Ledgers (aka Blockchain) & Alternative Investments
- Smart Ledger Geostamping - Steps Toward Interoperability & Standards
- Auditing Mutual Distributed Ledgers (aka Blockchains): A Foray Into Distributed Governance & Forensics
- Don't Let The Bitcoin Bubble Blind You To The Wonders Of Smart Ledger Technology
- The London Token Fundraising Manifesto
- Blockchain Could Help Us Reclaim Control Of Our Personal Data
- Why Financial Services Should Be Terrified Of Dispensing Wealth Management Robo-Advice
- Five Real Ways Distributed Ledgers Are Changing Payments
- Responsibility Without Power? The Governance Of Mutual Distributed Ledgers (aka Blockchains)
- Blockchain - Dark Currencies & The Risks
Media Coverage
- 20 April 2018: Technology And Smart Ledgers Are The Key To Averting A Global Trade Crisis
- 20 February 2018: Cardano Foundation and Z/Yen: Threat of Quantum Computing to Blockchain Security
- 20 February 2018: Cardano Foundation and Z/Yen Explore Threat Of Quantum Computing To Blockchain Security
- 04 December 2017: Cardano Foundation Selects Z/Yen For Blockchain Research Programme - Input From Cardano Blockchain Users Will Inform Research Priorities To Accelerate Potential Use Cases
- 04 December 2017: Cardano Foundation Partners With Z/Yen Group's Distributed Futures To Research Blockchain And AI
- 04 December 2017: Cardano Foundation Selects Z/Yen for Blockchain Research Programme
- 16 November 2017: Blockchain Is Unlocking The Future Of Banking
- 07 November 2017: The Review - Ask The Experts: Governance Of Cryptocurrencies
- 31 October 2017: Don't Let The Bitcoin Bubble Blind You To The Wonders Of Smart Ledger Technology
- 23 October 2017: 'London Token Fundraising Manifesto' Aims To Distinguish London As A World Leader In Cryptocurrency Investment
- 23 October 2017: The London Token Fundraising Manifesto
- 23 October 2017: London Token Fundraising Manifesto
- 23 October 2017: Z/Yen Group's Michael Mainelli Launches Voluntary Code For ICOs: London Token Fundraising Manifesto
- 28 September 2017: Blockchain World Interviews Michael Mainelli
- 15 September 2017: How To Adapt & Intergrade The Emerging Digital Landscape (eg DLT)
- 05 September 2017: The Cyberlaw Podcast - Interview With Michael Mainelli
- 24 August 2017: Researchers Bring Atomic Clock Timestamp Precision To Stock Trading Over Distributed Ledgers
- 24 August 2017: Blockchain 'Atomic Ledger' Experiment Records 20 Million Timestamped Stock Trades
- 24 August 2017: Researchers Bring Atomic Clock Timestamp Precision To Stock Market Trading
- 24 August 2017: Researchers Bring Atomic Clock Timestamp Precision To Stock Market Trading Over Distributed
- 08 August 2017: Responsibility Without Power? The Governance Of Mutual Distributed Ledgers (aka Blockchain): New Long Finance Report
- 18 June 2017: Universities Add Blockchain To Course List
- 05 June 2017: Blockchain-Related Job Adverts Surge
- 03 June 2017: Talk With Michael Mainelli By Paul Tanasyuk | Distributed Ledger And Identity
- 26 May 2017: What Is Blockchain and How Does It Work?
Events
- 30 April 2019: Distributed Futures Forum
- 17 January 2019 : Distributed Futures Forum
- 02 October 2018: Distributed Futures Forum
- 18 July 2018: Crash Course on Smart Ledgers (Blockchains)
- 26 June 2018: Crash Course on Smart Ledgers (Blockchains)
- 06 June 2018: Distributed Futures Forum
- 30 May 2018: Timestamping - Accuracy And Comparability
- 23 May 2018: Crash Course on Smart Ledgers (Blockchains)
- 17 May 2018: P&I Workshop
- 24 April 2018: Distributed Futures Forum
- 19 April 2018: The Economic Impact Of Smart Ledgers On World Trade
- 17 April 2018: Parliamentary Reception: The Economic Impact of Smart Ledgers On World Trade
- 10 April 2018: The Third Internet Of Agreements Conference: Identity
- 09 April 2018: Crash Course on Smart Ledgers (Blockchains)
- 21 March 2018: Liquidity Or Leakage - Plumbing Problems With Cryptocurrencies
- 07 March 2018: Get Smart About Scandals: Past Lessons For Future Finance
- 27 February 2018: Crash Course on Smart Ledgers (Blockchains)
- 23 February 2018: The Second Internet Of Agreements Conference: Blockchains And World Trade
- 20 February 2018: The Quantum Countdown: Quantum Computing And The Future Of Distributed Ledger Encryption
- 01 February 2018: Smart Ledgers - Learning From Past Financial Scandals